Understanding Ransomware
Ransomware is a malware designed to deny a user or organization access to files on their computer.- By encrypting these files and demanding a ransom payment for the decryption key, cyber attackers place organizations in a position where paying the ransom is the easiest and cheapest way to regain access to their files.
- Some variants have added additional functionality – such as data theft – to provide further incentive for Ransomware victims to pay the ransom.
- Ransomware has quickly become the most prominent and visible type of Malware. Recent ransomware attacks have impacted hospitals’ ability to provide crucial services, crippled public services in cities, and caused significant damage to various organizations.
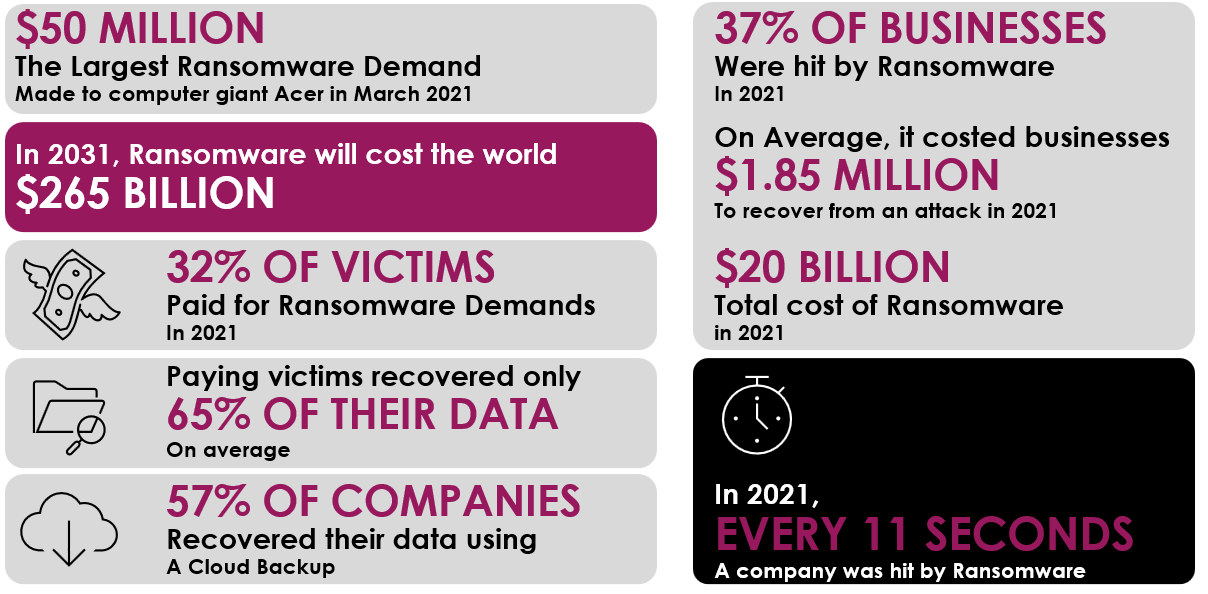
Ransomware by Numbers
Ransomware Readiness Assessment Services
The Ransomware Readiness assessment aligns organizations’ Ransomware prevention and mitigation requirements, objectives, risk appetite, and resources with the elements of the Cybersecurity Standards.The purpose of the profile is to help organizations identify and prioritize opportunities for improving their security and resilience against Ransomware attacks.
Ransomware’s main goal is to spread.
We help to stop that spread.
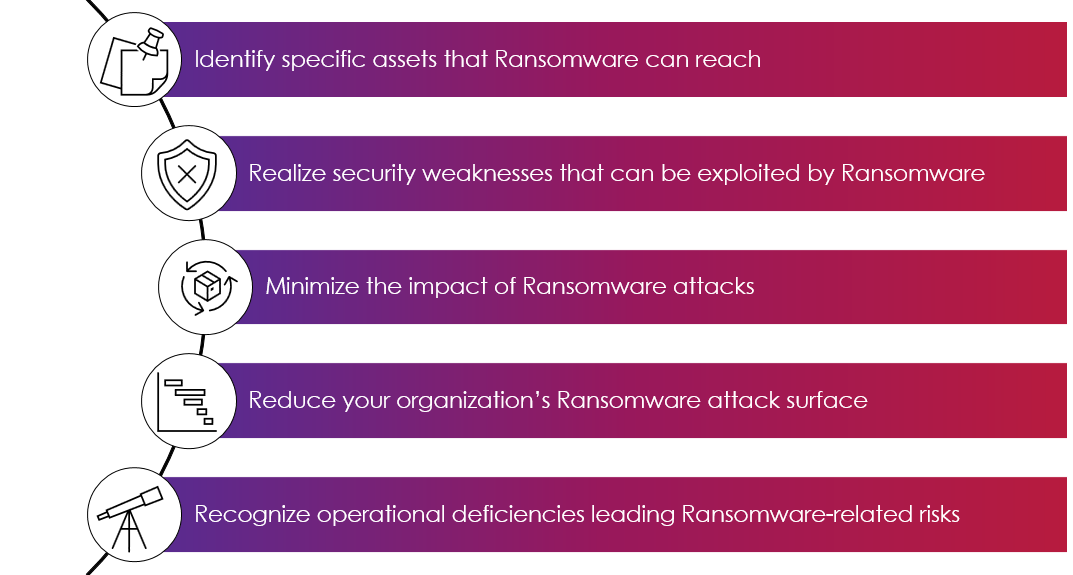
Our service is based upon the NIST Cybersecurity Framework approach and is comprised of the following five components.
Our Framework
Identify
identifying, locating, and classifying the critical business’ assets (both informational and digital) and confirming these with you.We will then conduct a ransomware vulnerability assessment against known risk scenarios identifying and documenting all existing anti-malware controls and mapping them to the confirmed business assets to verify the applicability and any detect gaps in protection.

Protect
Assess the effectiveness of the existing controls and processes implemented to mitigate an attack.These would typically include assessing:
- Data Back-up Methodology
- Network Segmentation
- Web Protection
- Mail Protection
- User Permission & Awareness
- Servers & Endpoint Configuration
- Change & Patch Management Processes

Detect
Assess how quickly your system and users detect the simulated attacks and report them to the appropriate business division or point of contactAnti-malware security software and hardware products would also be assessed.

Respond
Assess the business’s response to the simulated ransomware attacks.This is done through a table-top walk-through of the existing Incident Response Plan and monitoring the live exercise. The business Incident Response Plan and procedures are specifically assessed for efficiency and effectiveness. Team members are assessed for their execution of the plan and their professional skills and experience.

Recover
The business’ capability to recover from the simulated ransomware attacks.This is also done through table-top walk throughs of the existing Business Continuity and Disaster Recovery (BC/DR) plans to confirm their applicability to conditions resulting from the “live” exercise. System back-ups are verified, and documented business impact assessments (BIAs) are also assessed for their relevance and accuracy. BC/DR vendor solutions are also evaluated for efficiency and effectiveness in this final phase.
We offer benefits that matter
- Total protection against Cyberattacks, Ransomware & Data Breaches
- Identify & manage Vulnerabilities, Key Security Gaps and receive a custom-built remediation roadmap
- Help adhere to Compliances with various regulatory frameworks
- Secure applications on premises or on Cloud
- Help get onboarded with potential clients & partners by aligning to their Regulations & Expectations
- Holistic partnership approach to implement Security Controls
We deliver Cybersecurity for You!

People Focus
Evidenced through internal training programs, vast library of external training programs, investments in hiring the right people, upskilling and training people.

Innovation
Constant automation throughout each business unit, adoption of state-of-the-art technologies from leading cybersecurity vendors, development of enterprise tools like FireSec.
Systems and Process Focus
Documentation of standard operating processes, dedicate quality control function, massive internal knowledge base comprising 20+ years of experience, enabling employees to leverage off this and then innovate onwards.

People Focus
Evidenced through internal training programs, vast library of external training programs, investments in hiring the right people, upskilling and training people.

Innovation
Constant automation throughout each business unit, adoption of state-of-the-art technologies from leading cybersecurity vendors, development of enterprise tools like FireSec.

Systems and Process Focus
Documentation of standard operating processes, dedicate quality control function, massive internal knowledge base comprising 20+ years of experience, enabling employees to leverage off this and then innovate onwards.
Download our Ransomware Whitepaper today!